 Cloud computing is one of the hottest buzzwords in technology. It appears 48 million times on the Internet. But amidst all the chatter, there is one question about cloud computing that has never been answered: Who said it first?
Cloud computing is one of the hottest buzzwords in technology. It appears 48 million times on the Internet. But amidst all the chatter, there is one question about cloud computing that has never been answered: Who said it first?
Some accounts trace the birth of the term to 2006, when large companies such as Google and Amazon began using “cloud computing” to describe the new paradigm in which people are increasingly accessing software, computer power, and files over the Web instead of on their desktops.
But Technology Review tracked the coinage of the term back a decade earlier, to late 1996, and to an office park outside Houston. At the time, Netscape’s Web browser was the technology to be excited about, the Yankees were playing Atlanta in the World Series, and the Taliban was celebrating the sacking of Kabul. Inside the offices of Compaq Computer, a small group of technology executives was plotting the future of the Internet business and calling it “cloud computing.”
Their vision was detailed and prescient. Not only would all business software move to the Web, but what they termed “cloud computing-enabled applications” like consumer file storage would become common. For two men in the room, a Compaq marketing executive named George Favaloro and a young technologist named Sean O’Sullivan, cloud computing would have dramatically different outcomes. For Compaq, it was the start of a $2-billion-a-year business selling servers to Internet providers. For O’Sullivan’s startup venture, it was a step toward disenchantment and insolvency.
Cloud computing still doesn’t appear in the Oxford English Dictionary. But its use is spreading rapidlybecause it captures a historic shift in the IT industry as more computer memory, processing power, and apps are hosted in remote data centers, or the “cloud.” With billions of dollars of IT spending in play, the term itself has become a disputed prize. In 2008, Dell drew outrage from programmers after attempting to win a trademark on “cloud computing.” Other technology vendors, such as IBM and Oracle, have been accused of “cloud washing,” or misusing the phrase to describe older product lines.Like “Web 2.0,” cloud computing has become a ubiquitous piece of jargon that many tech executives find annoying, but also hard to avoid. “I hated it, but I finally gave in,” says Carl Bass, president and CEO of Autodesk, whose company unveiled a cloud-computing marketing campaign in September. “I didn’t think the term helped explain anything to people who didn’t already know what it is.”
The U.S. government has also had trouble with the term. After the country’s former IT czar, Vivek Kundra, pushed agencies to move to cheaper cloud services, procurement officials faced the question of what, exactly, counted as cloud computing. The government asked the National Institutes of Standards and Technology to come up with a definition. Its final draft, released this month, begins by cautioning that “cloud computing can and does mean different things to different people.”
“The cloud is a metaphor for the Internet. It’s a rebranding of the Internet,” says Reuven Cohen, cofounder of Cloud Camp, a course for programmers. “That is why there is a raging debate. By virtue of being a metaphor, it’s open to different interpretations.” And, he adds, “it’s worth money.”
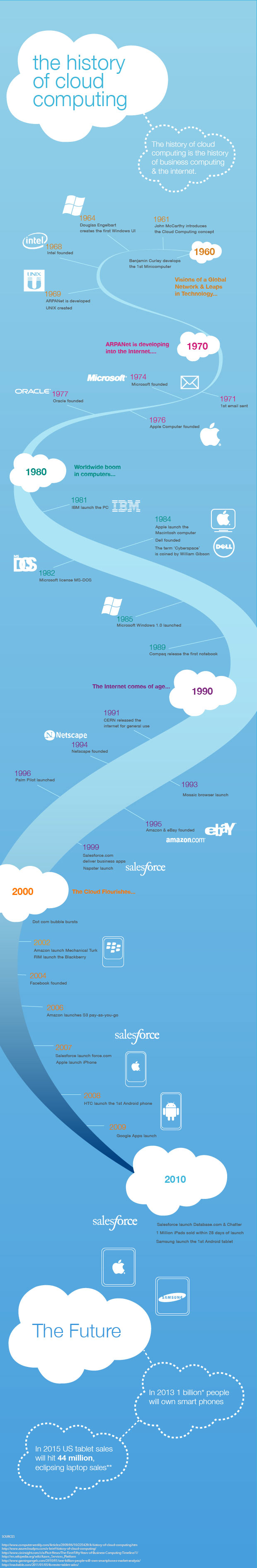
Part of the debate is who should get credit for inventing the idea. The notion of network-based computing dates to the 1960s, but many believe the first use of “cloud computing” in its modern context occurred on August 9, 2006, when then Google CEO Eric Schmidt introduced the term to an industry conference. “What’s interesting [now] is that there is an emergent new model,” Schmidt said, “I don’t think people have really understood how big this opportunity really is. It starts with the premise that the data services and architecture should be on servers. We call it cloud computing—they should be in a “cloud” somewhere.”
The term began to see wider use the following year, after companies including Amazon, Microsoft, and IBM started to tout cloud-computing efforts as well. That was also when it first appeared in newspaper articles, such as a New York Times report from November 15, 2007, that carried the headline “I.B.M. to Push ‘Cloud Computing,’ Using Data From Afar.” It described vague plans for “Internet-based supercomputing.”
Sam Johnston, director of cloud and IT services at Equinix, says cloud computing took hold among techies because it described something important. “We now had a common handle for a number of trends that we had been observing, such as the consumerization and commoditization of IT,” he wrote in an e-mail.
Johnston says it’s never been clear who coined the term. As an editor of the Wikipedia entry for cloud computing, Johnston keeps a close eye on any attempts at misappropriation. He was first to raise alarms about Dell’s trademark application and this summer he removed a citation from Wikipedia saying a professor at Emory had coined the phrase in the late 1990s. There have been “many attempts to coopt the term, as well as various claims of invention,” says Johnston.
That may explain why cloud watchers have generally disregarded or never learned of one unusually early usage—a May 1997 trademark application for “cloud computing” from a now-defunct company called NetCentric. The trademark application was for “educational services” such as “classes and seminars” and was never approved. But the use of the phrase was not coincidental. When Technology Review tracked down NetCentric’s founder, O’Sullivan, he agreed to help dig up paper copies of 15-year-old business plans from NetCentric and Compaq. The documents, written in late 1996, not only extensively use the phrase “cloud computing,” but also describe in accurate terms many of the ideas sweeping the Internet today…continue to source.